|
Actions by Friendly Force
|
|
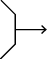
Attack by fire
|
|
The use of direct fires, supported by indirect fires, to engage an enemy force without closing with the enemy to destroy, suppress, fix, or deceive that enemy.
|
Overt actions where an origination (or interim relay) point can be determined, such as distributed denial-of-service attacks, broad intrusive scans, where these actions create the intended effect on the target.
|
|
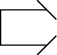
Breach
|
|
Break through or establish a passage through an enemy defense, obstacle, minefield, or fortification.
|
Noncredential-based access (penetration through a firewall, using an exploit or hacking tradecraft).
|
|
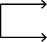
Bypass
|
|
Maneuver around an obstacle, position, or enemy force to maintain the momentum of the operation while deliberately avoiding combat with an enemy force.
|
Credential-based access (use captured credentials for login).
|
|
Clear
|

|
Remove all enemy forces and eliminate organized resistance within an assigned area.
|
Comprehensive scans and forensics, removing all malware and adversary points of presence and external connections.
|
|
Control
|
n/a
|
Maintain physical influence over a specified area to prevent its use by an enemy or to create conditions necessary for successful friendly operations.
|
Standard cybersecurity mission to protect a domain, typically assigned to a cyber security practitioner (CSP).
|
|
Counter-reconnaissance (Screen)
|
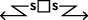
|
Provide early warning to the protected force.
|
Detection activities on a boundary or domain.
|
|
Counter-reconnaissance (Guard)
|
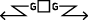
|
Protect the main body by fighting to gain time while also observing and reporting information and preventing enemy ground observation of and direct fire against the main body. Units conducting a guard mission cannot operate independently because they rely upon fires and combat support assets of the main body.
|
Domain-wide detection and hunt-type activities by a cyber protection Team or local defensive unit, augmenting the capabilities of a CSP.
|
|
Counter-reconnaissance
(Cover)
|
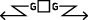
|
Protect the main body by fighting to gain time while also observing and reporting information and preventing enemy ground observation of and direct fire against the main body.
|
Domain-wide detection, hunt, and reposturing of defensive boundary controls by a CSP.
|
|
Exfiltrate
|

(No symbol exists. Symbol shows the flow of exfiltrated data, a substantial deviation from the existing definition of this task.)
|
Remove Soldiers or units from areas under enemy control by stealth, deception, surprise, or clandestine means.
|
Movement of data from its original location to a location under enemy control, typically by means of stealth, deception, or clandestine means.
|
|
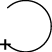
Occupy
|
|
Move a friendly force into an area so that it can control that area. Both the force’s movement to and occupation of the area occur without enemy opposition.
|
Deployment of a cyber protection team to a domain in advance of suspected adversary activity.
|
|
Retain
|

|
Ensure that a terrain feature controlled by a friendly force remains free of enemy occupation or use.
|
Defense of a network device or domain to prevent any adversary access.
|
|
Secure
|

|
Prevent a unit, facility, or geographical location from being damaged or destroyed as a result of enemy action.
|
Defense of a network device or domain to prevent an adversary from making any changes to data or functionality.
|
|
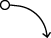
Seize
|
|
Take possession of a designated area by using overwhelming force.
|
Gain control of a device, network, data, or credentials. In cyberspace, two opposing forces may have simultaneous control of any or all of these assets.
|
|
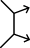
Support by fire
|
|
A maneuver force moves to a position where it can engage the enemy by direct fire in support of another maneuvering force.
|
Overt actions where an origination (or interim relay) point can be determined, such as distributed denial-of-service attacks, broad intrusive scans, and where these actions are designed to set the conditions for success for the primary attack actions.
|
|
Effects on Enemy Force
|
|
Block
|

|
Deny the enemy access to an area or prevent the enemy’s advance in a direction or along an avenue of approach.
Also an obstacle effect that integrates fire planning and obstacle efforts to stop an attacker along a specific avenue of approach or prevent the attacking force from passing through an engagement area.
|
Use or modification of blacklists, whitelists, access control lists, routing policies, credentials (username-password pairs, or machine-issued), or filters on firewalls, domain name servers, domain controllers, Web servers, email servers, or others to prohibit or terminate access based on specific criteria.
|
|
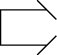
Canalize
|
|
Restrict enemy movement to a narrow zone by exploiting terrain coupled with the use of obstacles, fires, or friendly maneuver.
|
Use of routing policies, honeypots/honeyports/honeynets, or other defensive techniques to direct potential adversary traffic to desired network locations.
|
|
Contain
|
|
Stop, hold, or surround enemy forces or to cause them to center their activity on a given front and prevent them from withdrawing any part of their forces for use elsewhere.
|
Not strictly possible in cyberspace, since forces exist as a function of effort being expended. However, could be used to indicate quarantine of malware or emails.
|
|
Destroy
|

|
Physically render an enemy force combat-ineffective until it is reconstituted. Alternatively, to destroy a combat system is to damage it so badly that it cannot perform any function or be restored to a usable condition without being entirely rebuilt.
|
Deleting all files from a server, flashing basic input-output system or firmware, or causing physical damage to industrial control systems.
|
|
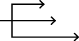
Disrupt
|
|
Integrates direct and indirect fires, terrain, and obstacles to upset an enemy’s formation or tempo, interrupt the enemy’s timetable, or cause enemy forces to commit prematurely or attack in a piecemeal fashion.
|
Interrupting connections periodically, enforcing time limits on sessions, or actions that require an enemy to repeat previous steps, upset an enemy’s tempo, interrupt the enemy’s timetable, or cause the enemy’s efforts to proceed in a piecemeal fashion.
|
|
Fix
|

|
Prevent the enemy force from moving any part of that force from a specific location for a specific period.
|
Not strictly possible in cyberspace, since forces exist as a function of effort being expended, but used to indicate actions that require an enemy to focus effort to restore function (for example, reboot a domain controller or data server following an induced system crash); to expend much greater effort than planned to obtain an objective (for example, consuming attacker resources using a realistic honeynet); or to refrain from using capabilities for fear of detection (for example, refrain from activating implants because of increased random scans for active malware).
|
|
Interdict
|
|
Prevent, disrupt, or delay the enemy’s use of an area or route.
|
Denial-of-network (data transport) services, or limiting access to services.
|
|
Isolate
|

|
Requires a unit to seal off—both physically and psychologically—an enemy from sources of support, deny the enemy freedom of movement, and prevent the isolated enemy force from having contact with other enemy forces.
|
Removal of a device infected with malware from the network, moving a phishing email from the server to a forensics sandbox.
|
|
Neutralize
|
|
Render enemy personnel or materiel incapable of interfering with a particular operation.
|
Any action taken against another cyberspace unit that prevents it from using its offensive or defensive capabilities (for example, interrupt the sensor feeds from a target domain to the responsible cyber defense unit).
|
|
* As described and depicted in various DOD sources, including MIL-STD-2525D, Joint Military Symbology, June 10, 2014; Field Manual (FM) 1-02/Marine Corps Reference Publication 5-12A, Operational Terms and Graphics, February 2, 2010 (incorporating Change 1); FM 3-90-1, Offense and Defense, vol. 1, March 2013; FM 3-90-2, Reconnaissance, Security and Tactical Enabling Tasks, vol. 2, March 2013.
|